|
|
Order by Related
- New Release
- Rate
Results in Title For encrypted
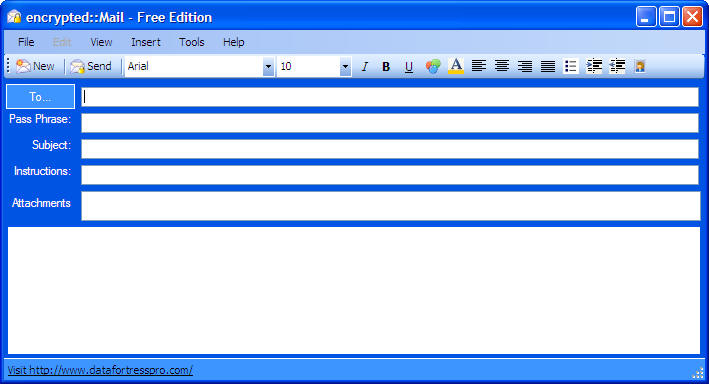 | encrypted::Mail allows users to send encrypted emails to anyone with ease, regardless of the users or recipients existing mail client. encrypted::Mail uses symmetric encryption and allows senders to add a pass phrase for additional security. .. |
|
 | Real powerful plug and play ,encrypted disk. prevent your personal documents from stole,very easy to use,one click operation, full shell menu operation help you for manage your disk image files.password retrieve feature prevent your password lost.Max 4 device for you. ..
|
|
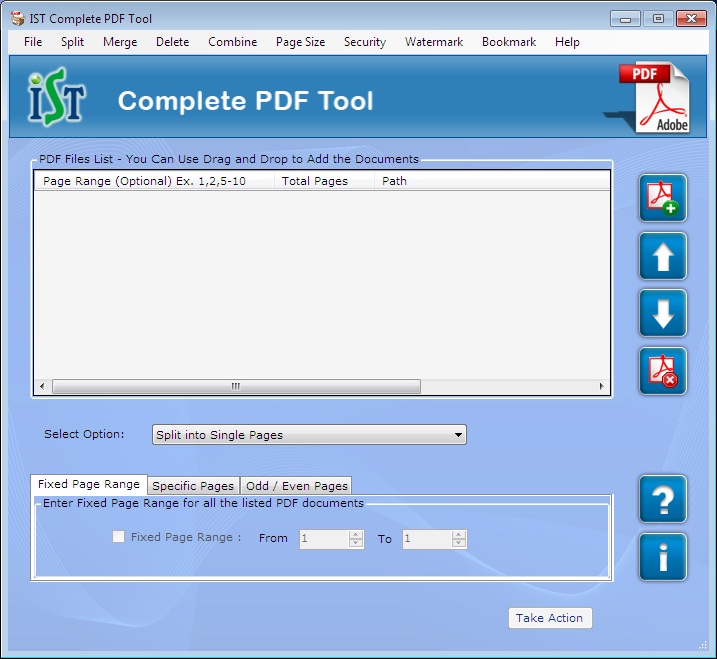 | PDF Password Encrypted for PDF as per requirement and merge split document of the several pages. PDF generator merger splitter software tool to generate password bookmark watermark stamp change page size delete unrequired pages in PDFs document. .. |
|
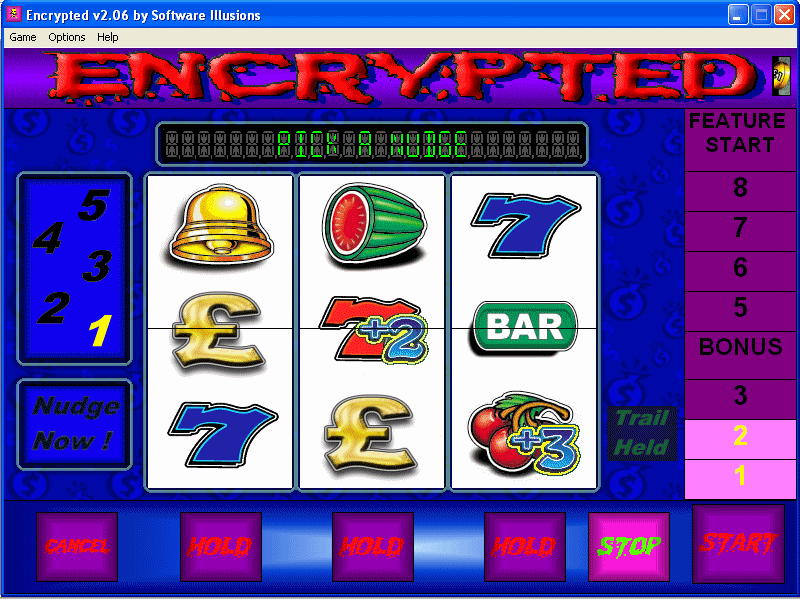 | Encrypted Fruit Machine, gamble for the virtual Jackpot! With a spooky theme, and based on a real UK style fruit machine this game will have you entertained for hours on end. ..
|
|
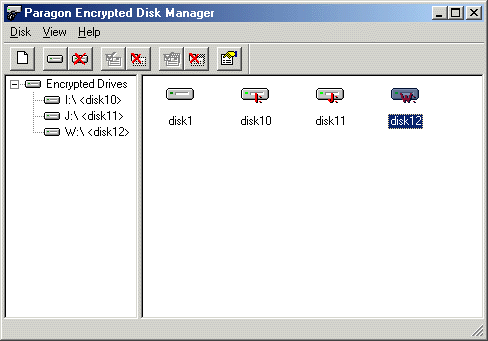 | Protect private and sensitive data from potential unauthorized access. No matter what is your particular needs, protecting your data on computer, sharing one computer between several persons or secured transfer of data to friend, co-worker or boss, Encrypted Disk will help you to fulfill your tasks. You can encrypt virtual disk image with one of modern and reliable encryption algorithms - Encrypted Disk supports Blowfish (448-bit key) and Triple DES (192-bit key). Encrypted disk can be mounted with any spare drive letter in the system, then every application and system process will have transparent access to the contents of encrypted virtual disk. You don't have to remember long and complex passwords, you can have key-file on a diskette or another removable media and use it to access encrypted disk image. Paragon Encrypted Disk is a system for those who are anxious for protection of their personal or professional information. The system allows to create virtual encrypted disks with all information on them encrypted and decrypted on the fly. The encrypted disk contents is stored as a binary file called the encrypted disk image. This file can reside on a hard drive, on a network drive, on removable media such as CD-ROM, JAZ, Zip, etc. Once an encrypted disk image is created it can be mounted as a virtual drive anytime and anywhere later. The disk image can be mounted only if a user enter an appropriate password or supply appropriate Key. Strong encryption algorithms used in the system guarantee that nobody can access your private information. .. |
|
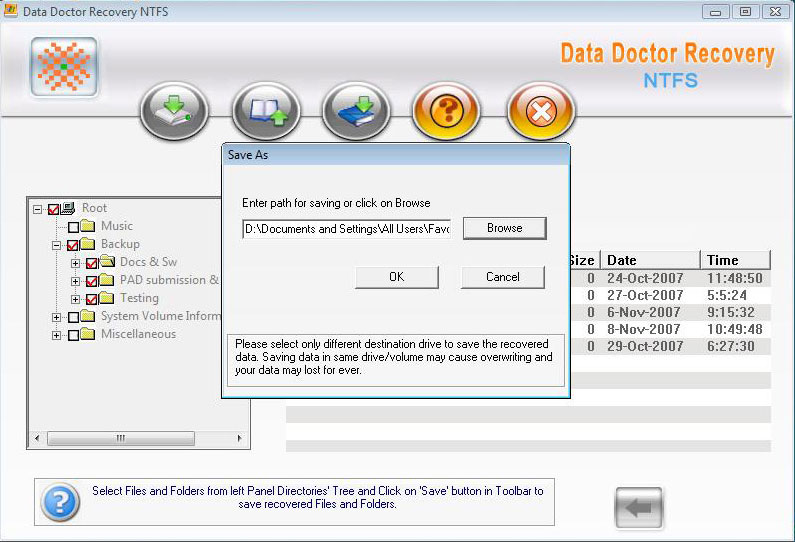 | Lost partition recovery software is a technically advance utility support recovery of accidental deleted data, compressed file, long file name, virus attack files etc. Data recovery program is compatible with Vista, XP sp2, 2000 and all Windows OS. ..
|
|
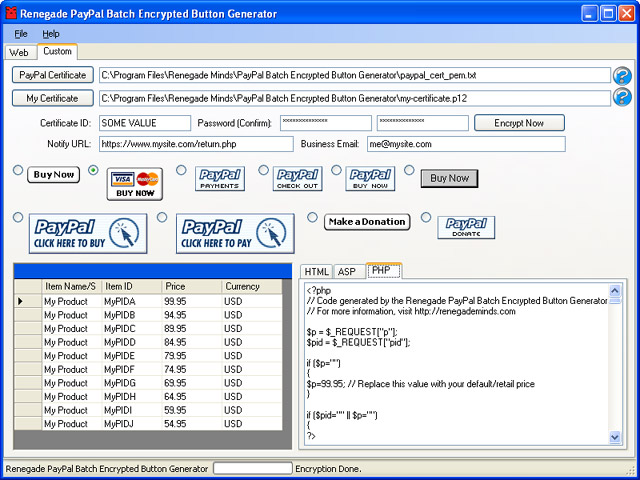 | Increase profits on product sales by offering time sensitive discounts that encourage visitors to become customers. Keep payments secure with PayPal secure encrypted buttons. Generate large batches in seconds with batch processing. Pays for itself. .. |
|
 | HandyCrypto allows you to hide folders and encrypt files with on-the-fly AES encryption. Just create one or more encrypted secure folders from local folders and move your sensitive files into the specified folder and they will be encrypted/decrypted in real-time. You can work with the files as usual, and when you're done, lock the briefcase, which will store the files securely and also hide the entire folder from view. Additional features include a password-protect interface, supports for FAT/FAT32/NTFS, and protection under Windows Safe Mode. Laptops users will find this tool to be very useful. With HandyCrypto, you will not worry about leak of sensitive business data any longer in case of the computer was stolen. This tool is foolproof, easy-to-use, and self-protected. .. |
|
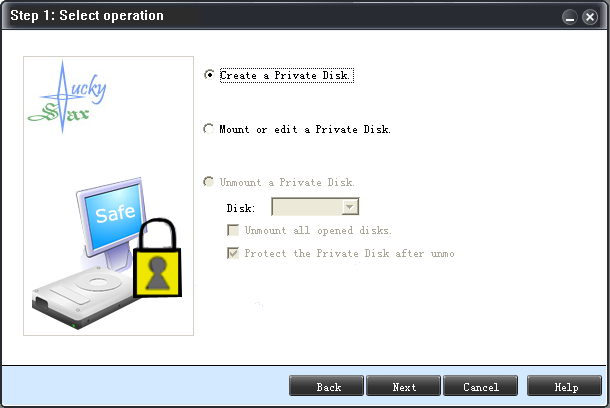 | This utility helps protect sensitive information largely without disrupting normal work, by creating a virtual disk that can hide a group of important files, all of which can be unlocked at once with a single password. .. |
|
 | Protect vital information on your PC with a secure and hidden vault by Cryptex. Feel better knowing that ANY file you lock in the vault will be protected with strong encryption to ensure maximum protection against theft and peeping eyes. .. |
|
Results in Keywords For encrypted
 | A combined 32 bit Windows 95/98/2000/ME client/server which incorporates strong blowfish encryption and the FTP protocol (RFC 959 implementation) to provide secure file transfers over the Internet. This program works 100% with other FTP Clients/Servers in non-encrypted mode, and provides strong encryption when the remote and local hosts both use EFTP. .. |
|
 | Peer2Peer Secure Instant Messenger and Chat
Your boss is spying you... YES! Every message/file you send on your lan can be intercepted by anyone...
X-COM can offer you a minimun of privacy: every communications is encrypted using the Blowfish encryption algorithm.
You will be able to send messages / files and chat with anyone on your lan and internet.
Features:
- encrypted communications (Blowfish / 56 bit):
- encrypted instant messenger
- encrypted public chat
- encrypted file transfer..
|
|
 | encrypted::Mail allows users to send encrypted emails to anyone with ease, regardless of the users or recipients existing mail client. encrypted::Mail uses symmetric encryption and allows senders to add a pass phrase for additional security. .. |
|
 | Real powerful plug and play ,encrypted disk. prevent your personal documents from stole,very easy to use,one click operation, full shell menu operation help you for manage your disk image files.password retrieve feature prevent your password lost.Max 4 device for you...
|
|
 | An ideal utility to store encrypted images and other files and view them easily and securely. Stores files in encrypted archives. File names, size, and data are encrypted. The individual file boundaries cannot be distinguished. On-the-fly instant decryption for images and text. Fully standards compatible: AES AES encryption up to 256 bit (in CBC mode); key generation based on PKSC5 and SHA256. No installation required. Requires .NET... |
|
 | This shareware allows you to encrypt/lock, decrypt/unlock files and folders, based on your needs. You also could use this shareware to run an encrypted file or encrypted folder of your chosen, and the file or folder in question remains encrypted/locked after the execution. Moreover, this is a fully functional 30-day shareware. Try it now!..
|
|
 | Free Encryption Software, Lock, hide, and password-protect all types of files and folders. Creates multiple encrypted container (vault) to protect your data. It's powerful encryption ensures that only you can access your data... |
|
 | Using PrivateZone, you can keep your letters, databases, photos, musics, movies and other private information in encrypted form on your hard disks, removable media, CD ROMs, floppies or network disks - all within a standard operating environment. .. |
|
 | PSM Encryptor is a cryptography and steganography tool. PSM Encryptor will encrypt any group of files (including whole directory structures) but will also disguise the resulting encrypted archive as a working sound or image file. Encrypts video too... |
|
 | TrueCrypt is a software system for establishing and maintaining an on-the-fly-encrypted drive. On-the-fly encryption means that data are automatically encrypted or decrypted right before they are loaded or saved, without any user intervention. No data stored on an encrypted volume can be read (decrypted) without using the correct password or correct encryption key. Until decrypted, a TrueCrypt volume appears to be nothing more than a series of random numbers. The entire file system is encrypted (i.e., file names, folder names, contents of every file, and free space).
This program is the real deal. Unlike other folder locking applications that can be circumvented by booting in safe mode or booting from a cd (or even worse, by terminating the process in Task Manager), the only way to access the data is to mount it using TrueCrypt. The best thing about TrueCrypt is that it is extremely fast... |
|
Results in Description For encrypted
 | Lists most encrypted word processor, database, spreadsheet and financial program files that are identified as encrypted. .. |
|
 | BladeBox creates virtual encrypted volumes, which are AES-ENCRYPTED files which can be mounted as if they were disk drives (with a DOS drive letter too). Virtual Encrypted Volumes (VEV) are seen and considered by the operating system as if they were actual volumes (drives), they have a drive letter, a volume name, and you can see them inside your My Computer resources and inside the Windows Explorer.BUT actually they are transparently encrypted files on disk. Every time you write or read data to those volumes, the data buffer is transparently encrypted/decrypted on-the-fly. The key concept for security is that data on disk ALWAYS remain encrypted. BladeBox gives System Administrators full control over network deployment of Virtual Encrypted Volumes by providing support for an administrative master password. Volumes can be automatically unmounted after XX (user-defined) minutes of inactivity or they can be quickly and silently unmounted by pressing the proper hot-key (special combination of keys)...
|
|
 | It's really easy to hide, encrypt and password protect data with CryptArchiver.
All you do is drag-and-drop your important files and folders into an encrypted drive - just like an ordinary drive! CryptArchiver has an intuitive and easy-to-use interface.
CryptArchiver Lite is encryption software for the desktop. It creates a special Encrypted Drive that can only be accessed with a password. Files stored in this drive are automatically encrypted on-the-fly. Once loaded, the encrypted drive is like any other drive.
When you unload the encrypted drive, it disappears from Windows! No one can access your data without the password. Load the Encrypted Drive again with the password, to access your files.
You can protect all types of files - be it email, databases, spreadsheets, text, graphics, audio or even video. You can even make encrypted backups of your files easily on your hard drive, or on external drives like CDs, DVDs, or USB devices. What's more, you can even install and run programs that are accessible and visible only to you!
Secure your important files and folders - get CryptArchiver today!.. |
|
 | JvCrypt is a powerful encryption and compression utility that allows you to create encrypted files and text messages with up to 448-bit encryption using the advanced Blowfish encryption algorithm. Some of JvCrypt's key features include: (1) Ability to protect your files with powerful encryption. With JvCrypt you can select a single file or multiple files to be compressed and encrypted all in one step. You have the option of creating a single encrypted zip file for each file selected or combining all of your selected files to a single encrypted zip file with a password of your choice. (2) Remove source files after they have been encrypted. With JvCrypt, you have the option of removing the source file or files after they have been encrypted. This option allows you to select a file or files, zip the files, encrypt the zip files and finally remove the non-encrypted files after the encrypted file has been created all in one step! (3) Decrypt encrypted zip files. Decrypt an encrypted zip file with ONLY the password that was used to create the encrypted zip file. Encrypted zip files will all have a file extension of .enz and only JvCrypt will be able to decrypt such files (assuming you have the correct password).
(4) Encrypt/Decrypt files from the command line. With JvCrypt, you can encrypt and decrypt files directly from the command line (DOS window). You can even execute JvCrypt commands from batch files! (5) Password database. With JvCrypt, you have the option of storing frequently used passwords into a password database. These passwords can be used when running JvCrypt from the command line or during normal interactive mode. You can even setup JvCrypt to require a password when starting! This will prevent anybody else from accessing your stored password database...
|
|
 | Protect private and sensitive data from potential unauthorized access. No matter what is your particular needs, protecting your data on computer, sharing one computer between several persons or secured transfer of data to friend, co-worker or boss, Encrypted Disk will help you to fulfill your tasks. You can encrypt virtual disk image with one of modern and reliable encryption algorithms - Encrypted Disk supports Blowfish (448-bit key) and Triple DES (192-bit key). Encrypted disk can be mounted with any spare drive letter in the system, then every application and system process will have transparent access to the contents of encrypted virtual disk. You don't have to remember long and complex passwords, you can have key-file on a diskette or another removable media and use it to access encrypted disk image. Paragon Encrypted Disk is a system for those who are anxious for protection of their personal or professional information. The system allows to create virtual encrypted disks with all information on them encrypted and decrypted on the fly. The encrypted disk contents is stored as a binary file called the encrypted disk image. This file can reside on a hard drive, on a network drive, on removable media such as CD-ROM, JAZ, Zip, etc. Once an encrypted disk image is created it can be mounted as a virtual drive anytime and anywhere later. The disk image can be mounted only if a user enter an appropriate password or supply appropriate Key. Strong encryption algorithms used in the system guarantee that nobody can access your private information... |
|
 | Send encrypted messages through email, save and retrieve encrypted documents. Due to server problems, we had to split zip file in two. Instructions for download are availableby clicking on the link ..
|
|
 | P-Encryption Suite is a powerful encryption program for the windows operating system used to store your private documents into a single encrypted file. There are two different encrypted archives P-Encryption Suite can create, Stealth and Normal. Stealth archives are PES archives disguised as a different file, such as an image or audio file. You can also take your encrypted data with you anywhere you go by using CD/DVD encryption... |
|
 | An ideal utility to store encrypted images and other files and view them easily and securely. Stores files in encrypted archives. File names, size, and data are encrypted. The individual file boundaries cannot be distinguished. On-the-fly instant decryption for images and text. Fully standards compatible: AES AES encryption up to 256 bit (in CBC mode); key generation based on PKSC5 and SHA256. No installation required. Requires .NET... |
|
 | A freeware decryption program that will allow anyone anywhere to view a Navaho Lock encrypted message (ifthey know the password). The decrypted file is only opened in memory. When the user closes the file it reverts to its encrypted state, leaving no trace of itself on the hard .. |
|
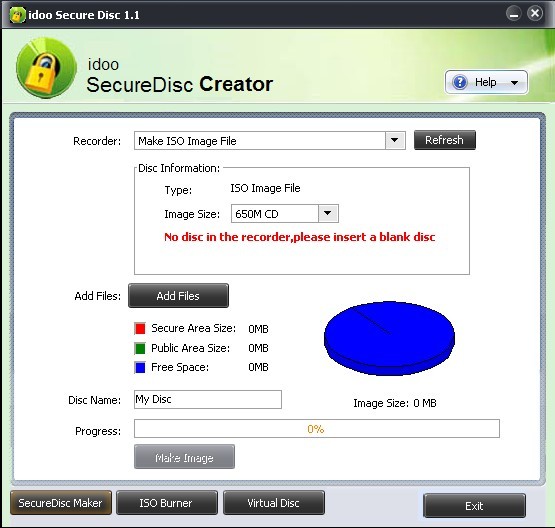 | idoo Secute Disc Creator, your can burn password-protected and encrypted discs. It supports most of CD DVD, if you have a recorder and you want to burn an portable encrypted disc... |
|
Results in Tags For encrypted
 | Protect private and sensitive data from potential unauthorized access. No matter what is your particular needs, protecting your data on computer, sharing one computer between several persons or secured transfer of data to friend, co-worker or boss, Encrypted Disk will help you to fulfill your tasks. You can encrypt virtual disk image with one of modern and reliable encryption algorithms - Encrypted Disk supports Blowfish (448-bit key) and Triple DES (192-bit key). Encrypted disk can be mounted with any spare drive letter in the system, then every application and system process will have transparent access to the contents of encrypted virtual disk. You don't have to remember long and complex passwords, you can have key-file on a diskette or another removable media and use it to access encrypted disk image. Paragon Encrypted Disk is a system for those who are anxious for protection of their personal or professional information. The system allows to create virtual encrypted disks with all information on them encrypted and decrypted on the fly. The encrypted disk contents is stored as a binary file called the encrypted disk image. This file can reside on a hard drive, on a network drive, on removable media such as CD-ROM, JAZ, Zip, etc. Once an encrypted disk image is created it can be mounted as a virtual drive anytime and anywhere later. The disk image can be mounted only if a user enter an appropriate password or supply appropriate Key. Strong encryption algorithms used in the system guarantee that nobody can access your private information... |
|
 | BladeBox creates virtual encrypted volumes, which are AES-ENCRYPTED files which can be mounted as if they were disk drives (with a DOS drive letter too). Virtual Encrypted Volumes (VEV) are seen and considered by the operating system as if they were actual volumes (drives), they have a drive letter, a volume name, and you can see them inside your My Computer resources and inside the Windows Explorer.BUT actually they are transparently encrypted files on disk. Every time you write or read data to those volumes, the data buffer is transparently encrypted/decrypted on-the-fly. The key concept for security is that data on disk ALWAYS remain encrypted. BladeBox gives System Administrators full control over network deployment of Virtual Encrypted Volumes by providing support for an administrative master password. Volumes can be automatically unmounted after XX (user-defined) minutes of inactivity or they can be quickly and silently unmounted by pressing the proper hot-key (special combination of keys)...
|
|
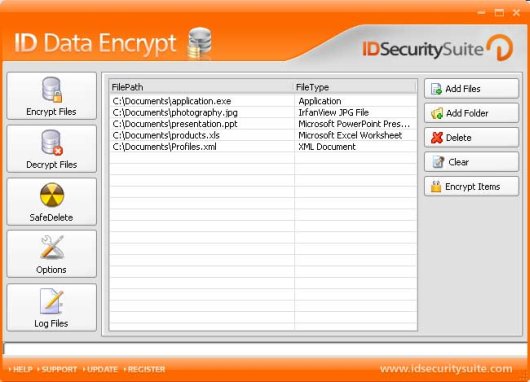 | ID Data Encrypt is a high-priority security program, responsible for your computer's real-time protection against hackers. It blocks access to unauthorized attempts to use your computer by making sure your computer stays safe from exposure to internal network attacks as well as external Internet ones.
Main Features:
- Encrypts files and folders
- Decrypts encrypted files
- Runs very quickly and efficiently
- Uses reliable algorithms
- Safely deletes or saves encrypted files
Detailed features:
- Encrypts all of the files you wish to keep private. If you need to keep files, folders and even complete directory trees away from anybody else's eyes, you can safely encrypt those files, keeping them under a password secure system.
- Retains a cryptographic library including the most reliable algorithms: Blowfish, Cast128, Gost, RC2, Rijndael and Twofish. ID Data Encrypt allows you to decide exactly how you want your data to be encrypted by providing a list with names and speed of each one of those algorithms.
- Decrypts encrypted files by the use of the same algorithms. It preserves the original content of the files before encrypting and restores them completely with no data damage.
- Extremely easy to use. ID Data Encrypt has a simple and convenient graphic interface, making it accessible for anyone to use. It also requires minimum space on your disk and runs fast and efficient by encrypting data in very shot time.
- Preserves or deletes files after being encrypted. ID Data Encrypt gives you the possibility to maintain on your computer the files that have encrypted or you can safely and permanently remove to maintain your privacy.
- Deletes or preserves encrypted files after they have been decrypted. You can still keep a sample of an encrypted file or folder on your computer even if you decrypted it.
- Securely wipes files and clears all tracks of where the file has been making it impossible for someone else to recover your deleted files... |
|
 | There are many tools on the market today that allow you to securely encrypt your files. They all have the same downside, though. They require an extra operation to be performed when you encrypt or decrypt your file. Here are the two common scenarios: You edit a document and save it to a file. Then you encrypt this file with your encryption program. And vise versa. You decrypt a file and then view/edit it in your text processor. It takes more time and requires you to perform more actions.
Some encryption programs allow you to create encrypted disk volumes. They encrypt and decrypt your files on-the-fly. Yet, there are definitely more downsides. If an encrypted volume is damaged, you lose all the files it contains. To use an encrypted disk volume on another computer, you need to install your disk encryption software on that computer.
Altstone offers an interesting solution. Their Private Notetaker is a highly portable application that combines a text processor and an encryption program. The program can operate in two modes: rich text and plain text, and thus, substitutes for both Wordpad and Notepad as their secure analogs. It automatically encrypts each file using the Blowfish algorithm and also allows you to protect files with individual passwords.
No extra operations required. You save and open files as you do with standard text editors. No encrypted disk volumes are created and thus no additional system resources are used. If a file gets damaged, you lose only this file and not the whole disk volume. "Portable" means that you can bring Private Notetaker with you and use it on any computer you have access to. No administrator rights required. Just put it on an USB drive and safely work with your documents wherever you go.
When you register the software, they develop a custom build for you containing your very own private key. This ensures the highest level of security. Files that you save, can be read only with your own copy of Private Notetaker...
|
|
 | Increase profits on product sales by offering time sensitive discounts that encourage visitors to become customers. Keep payments secure with PayPal secure encrypted buttons. Generate large batches in seconds with batch processing. Pays for itself... |
|
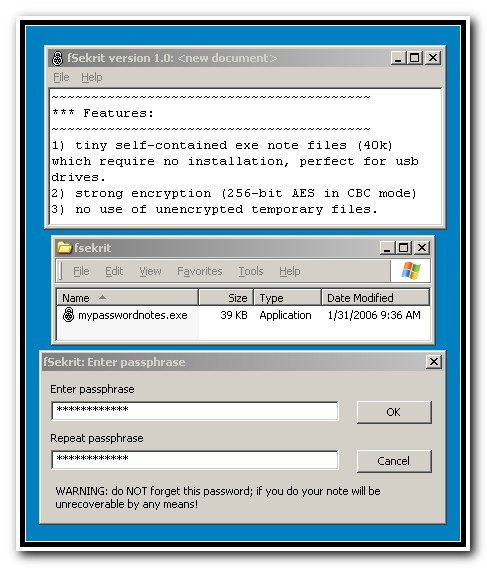 | fSekrit allows you to read and edit encrypted notes using self-contained tiny program files; completely portable - run from usb thumbdrives, etc. no need to install anything...
|
|
 | JvEncrypt utilizes the advanced Blowfish encryption algorithm and supports the following featuresEncrypt a string and add your own optional key to the encrypted output. Encrypt a string and output the encrypted value in hexadecimal format.Decrypt a string containing an optional key.Decrypt a string that utilized hexadecimal encrypted output.Encrypt a file and add your own optional key to the encrypted output. Decrypt a file containing an optional key.Compress a file or string prior to encrypting it. This allows for faster encryption.Uncompress a file or string prior to decrypting it. /olWith JvEncrypt, you can simply add the ActiveX control to your project and you are ready to go.. |
|
 | HandyCrypto allows you to hide folders and encrypt files with on-the-fly AES encryption. Just create one or more encrypted secure folders from local folders and move your sensitive files into the specified folder and they will be encrypted/decrypted in real-time. You can work with the files as usual, and when you're done, lock the briefcase, which will store the files securely and also hide the entire folder from view. Additional features include a password-protect interface, supports for FAT/FAT32/NTFS, and protection under Windows Safe Mode. Laptops users will find this tool to be very useful. With HandyCrypto, you will not worry about leak of sensitive business data any longer in case of the computer was stolen. This tool is foolproof, easy-to-use, and self-protected... |
|
 | Software protection tool. Its purpose is to selectively encrypt fragments of code in the program and add special code for stop debugging and disassembling. Features include:- polymorphic encryption with no constant signatures in encrypted fragments; - encrypted fragment will only be decrypted immediately before its execution; after the execution of the particular fragment it will be encrypted again (at any time during the execution there is only one protected fragment decrypted) - encryption has unlimited nesting (encrypted block inside encrypted block inside...) - single-use fragments: it is possible to mark a fragment of code so that fragment will be erased after the very first execution - user-key encryption - detect SoftIce, NtIce, FrogIce, TD and other debugger - detect registry/filesystem/API monitors - counteraction to dumping application with tools like ProcDump - anti-tracing measures - anti-disassembler measures - direct WinAPI support working around import table. - full integration with HardKey registration keymanager EXECryptor can protect any 32bit PE executable files. It was tested under W95/98/ME/2000/NT/XP. SDK available for Delphi, CBuilder, MSVC. .. |
|
 | encrypted::Mail allows users to send encrypted emails to anyone with ease, regardless of the users or recipients existing mail client. encrypted::Mail uses symmetric encryption and allows senders to add a pass phrase for additional security. .. |
|
Related search : ncrypted volumesvirtual encrypted,virtual encrypted volumesbladebox iron editiondata encryptencrypted files,decrypts encrypted filesprivate notetakerencrypted disk,encrypted disk volumesbatch encryptedpaypal batchbutton generatorencrypted buttonencryOrder by Related
- New Release
- Rate
encrypted passwords -
encrypted dvds -
usb encrypted -
encrypted email -
encrypted google -
|
|





















